NSF Research Experiences for Undergraduates (REU)
Summer 2010 - Computer Vision and Multi-Agent Systems
Department of Computer Science, Utah State University
Quentin Mayo

Name:
Quentin MayoMajor:
Computer ScienceSchool:
Jacksonville State UniversityHome Town:
Tuskegee, AlabamaAbout Me
I'm a senior(4th year) at Jacksonville State University. From an early age, I knew I loved computers. It was only natural that I majored in Computer Science.Prior to interning at Utah, I interned at UC Berkeley and Tuskegee University but I still didn't know what to expect. I knew that every REU was different. Nevertheless, I was surprised! Everything about the program was amazing. Instead of being mentored on everything you did, we where able to do projects we were interested in. Just like in real life, some projects fail, others had success, but in the end you learned something. Maybe some people didn't revise the wheel but their research showed what might be a wrong direction.
As far as other thing beyond research, there was a lot to do. The mentors encourage us to be active We had many bike trails, rock climbing, swimming, and so much more. We manage to be able to canoeing during one day in the program. A lot of the time I found myself running through the near by town and working-out in the HYPE. They had a amazing gym. I could get a great workout with all the equipment they offered.
In the end, I just LOVE my experience at USU.
Project
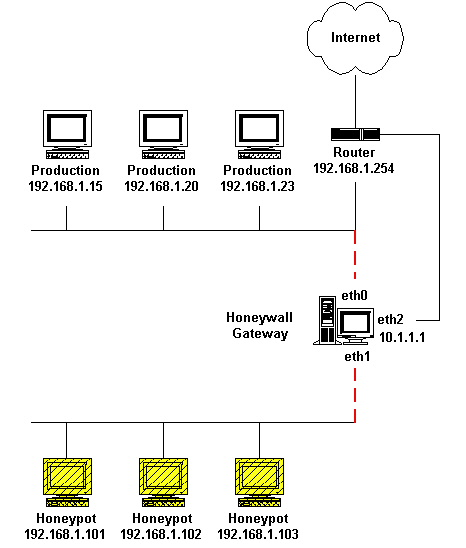
-->During the summer, I wrote a paper that give an introduction into honeypots and botnets. The paper was also a collection of literature involving honeypots. It give a general outline of different implementations of a High-Level Honey-pot and unique advantages and disadvantages. There was a detail explanation on common configurations and software being used in the industry. Although I wish I could have had the chance to analysis malicious software, issues involving networking and security prevented it.
Results
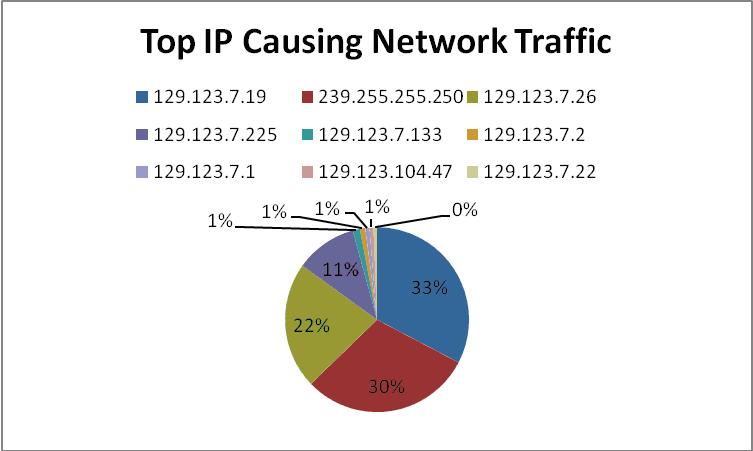
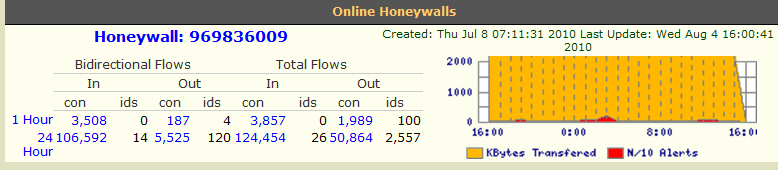
Although Honey-wall is a great application for implementing a Honey-pot, keeping other computers secure, and collecting data, there are a lot of false positives during execution. More than 70% of the alerts given were connections with USU. Even though the Honey-wall allows the user to restrict specific IP address, restricting USU traffic would just be similar to putting the honeypot in RM Mode. Disabling USU would render the honey-pot traffic unusable and most botnet will not executed without communication from the botmaster.Out of the many false positives, two IP address found had significations issues. Any connections on system that was technical IDLE could be considered malicious. 174.0.214.81 was listed in RBL (Real-Time Blocking List)’s SORBS Listed for Spamming. It made a call to one of the honeypots once but never again. Although the host name yt118.com was not list on the RBL, the Honey-pot connected to 222.77.178.53 which is Host name is yt118.com. yt118.com was listed on top 100 sites for malware activity by SMH. These sites were know for trying to entice users to download malicious software.
More in depth results can be found in my final presentation or final project.
Feel free to write me at: quentinmayo@yahoo.com